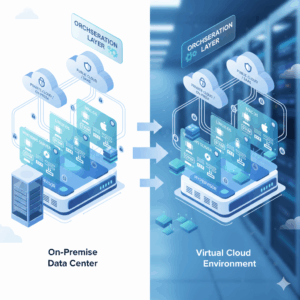
Virtualization technology is a core component of modern enterprise IT architecture. It enables abstraction of physical hardware resources into software-defined virtual environments, allowing multiple isolated operating systems to run concurrently on a single host machine. This approach forms the backbone of cloud computing, DevOps pipelines, cybersecurity labs, and enterprise data centers.
Virtualization Architecture Explained
At a technical level, virtualization introduces an abstraction layer between physical hardware and operating systems. This layer is managed by a hypervisor, which controls CPU scheduling, memory allocation, storage I/O, and network virtualization.
Core Components:
- Physical Host Hardware
- Hypervisor Layer
- Guest Operating Systems
- Virtualized Storage & Networking
This architecture ensures optimal performance, fault isolation, and scalability.
Virtual Machines and Resource Allocation
A virtual machine (VM) operates as an isolated execution environment with assigned virtual CPUs (vCPUs), memory, disk, and network interfaces.
Advanced virtualization platforms support:
- Dynamic memory allocation
- Live migration (vMotion)
- Snapshot-based backups
- High availability (HA)
These capabilities are critical for enterprise-grade workloads.
Hypervisors: Type 1 vs Type 2 (Technical Comparison)
Type 1 Hypervisors (Bare Metal)
- Direct hardware access
- Lower latency
- Used in data centre’s
- Examples: VMware ESXi, Hyper-V, KVM
Type 2 Hypervisors (Hosted)
- Runs on host OS
- Higher overhead
- Used for development/testing
- Examples: VirtualBox, VMware Workstation
Virtualization in Cloud and Hybrid Environments
Cloud providers rely on virtualization to deliver Infrastructure as a Service (IaaS). Virtual networks, storage pools, and compute instances are dynamically provisioned using virtualization orchestration tools.
In hybrid cloud environments, virtualization enables seamless workload migration between on-premise and cloud infrastructure.
Security Implications of Virtualization
Virtualization enhances security through isolation but also introduces new attack surfaces such as:
- Hypervisor vulnerabilities
- VM escape attacks
- Misconfigured virtual networks
Proper segmentation, patching, and access control are essential.
Enterprise Benefits of Virtualization
- Reduced CAPEX and OPEX
- Improved uptime and disaster recovery
- Faster application deployment
- Simplified infrastructure management
Conclusion
Virtualization technology remains a foundational skill for IT professionals working in cloud computing, cybersecurity, and enterprise infrastructure. Mastery of hypervisors, virtual machines, and virtualization architecture is essential for modern digital environments.